Installing Keycloak on Kubernetes: A Comprehensive Tutorial
Introduction
In the ever-evolving landscape of application security, Keycloak emerges as a beacon of reliability. This article dives into the realm of Keycloak, exploring its capabilities and guiding you through the essentials. Brace yourself for a journey into the heart of robust authentication and authorization.
Understanding Keycloak
At its core, Keycloak is an open-source identity and access management solution. Developed by Red Hat, it empowers developers to secure their applications with ease. The beauty of Keycloak lies in its flexibility—it seamlessly integrates with various platforms, making it a versatile choice for authentication and authorization needs.
Key Features that Make Keycloak Shine
Single Sign-On (SSO)
Bid farewell to the hassle of remembering multiple passwords. Keycloak introduces a Single Sign-On (SSO) experience, allowing users to access multiple applications with just one set of credentials. Say hello to convenience and goodbye to password fatigue.
User Federation
Keycloak opens the door to user federation, enabling seamless integration with existing user databases. Whether it's LDAP, Active Directory, or social media logins, Keycloak harmonizes diverse user sources under one roof.
Multi-Factor Authentication (MFA)
In a world where security is paramount, Keycloak steps up with Multi-Factor Authentication. Add an extra layer of protection by incorporating factors like SMS, email, or authentication apps. Your fortress just got stronger.
Authorization Services
Fine-tune access control with Keycloak's robust authorization services. Define policies, manage roles, and ensure that users have precisely the right level of access. Security tailored to your application's needs.
The Keycloak Installation Ballet on Kubernetes
Prerequisites: Setting the Stage
Before you dance with Keycloak on Kubernetes, ensure your stage is set. Check Kubernetes compatibility, create a dedicated namespace, and establish persistent storage. A well-prepared stage ensures a flawless performance.
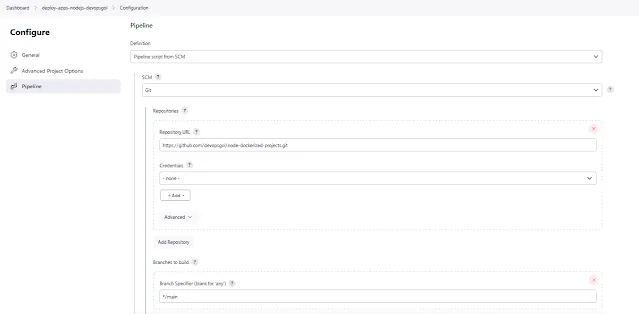
Step-by-Step Deployment with Helm
Enter Helm, the virtuoso of Kubernetes deployment. Learn the steps to deploy Keycloak effortlessly using Helm charts. It's a symphony of simplicity that transforms installation into an art.
Configuring Realms and Clients
Now that Keycloak graces your Kubernetes ensemble, it's time to tailor its performance. Dive into configuring realms and clients, molding Keycloak to fit your application's unique contours.
Fortifying Security
No ballet is complete without a strong finale. Explore the best practices for securing your Keycloak installation—configure SSL, implement robust authentication, and fortify authorization mechanisms.
Troubleshooting Pas de Deux
Even the most graceful ballet encounters hiccups. Navigate through common issues like database connection glitches and configuration snags. Transform challenges into a dance of triumph.
Conclusion: Applause for a Secure Future
Congratulations! You've waltzed through the installation of Keycloak on Kubernetes. With Keycloak as your partner, step into a future where security is not just a feature but a masterpiece.
FAQs: Unveiling Keycloak's Secrets
- Can Keycloak integrate with various user databases?Absolutely! Keycloak's user federation capabilities harmonize diverse user sources seamlessly.
- Why is Multi-Factor Authentication crucial in Keycloak?MFA adds an extra layer of security, fortifying your fortress against potential threats.
- How does Keycloak simplify access control?Keycloak's authorization services allow you to define precise policies, ensuring tailored access for users.
- Is Keycloak compatible with Kubernetes?Indeed! Ensure a smooth performance by checking Kubernetes compatibility before installation.
- What are the prerequisites for Keycloak installation on Kubernetes?Prepare your stage by checking compatibility, creating a namespace, and setting up persistent storage.
Dive into the world of Keycloak—an orchestra of security, simplicity, and versatility. Install Keycloak now and step into a future where authentication and authorization are not just features but an art.